The MotW Unofficial Patch for Windows still lacks an IOC
A maliciously signed file can bypass Mark-of-the-Web (MotW) security measures thanks to an actively exploited security hole in Microsoft Windows that has an unauthorized fix available.
Threat actors can employ malicious standalone JavaScript files to get around Mark-of-the-web security warnings thanks to a Windows zero-day vulnerability. The Windows security alert that appears when attempting to open a file from the Internet is the Mark-of-the-web security feature. If you open Internet files from an unreliable or suspicious source, your computer may become damaged.
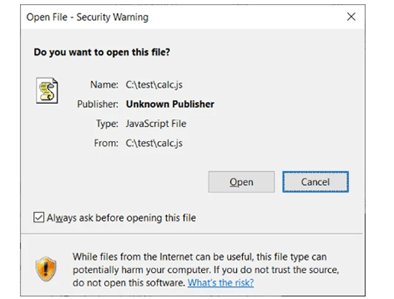
The blog released by AVERTIUM, Confirms that there are no known IOCs associated with the Mark-of-the-web vulnerability.
AVERTIUM said "At this time, there are no known IoCs associated with the Mark-of-the-web vulnerability. Avertium’s threat hunters remain vigilant in locating IoCs for our customers. Should any be located, Avertium will disclose them as soon as possible. For more information on how Avertium can help protect your organization, please reach out to your Avertium Service Delivery Manager or Account Executive".
AVERTIUM recommends:
- It is advisable that you do not open documents from unknown or suspicious sources.
- If you already are a 0patch user, the micro-patch is available on all online 0patch Agents. If you are new to the 0pach platform, you can create a new account here, where you can receive an automatic patch application without rebooting your device.



