Qbot malware now uses windows calculator to infect devices
Cyble analyst during a routine threat-hunting exercise found that Qbot malware has now begun using Windows Calculator to DDL side-load the malicious payload on infected computers.
Qbot (aka Qakbot, Quakbot, and Pinkslipbot) is a modular Windows malware strain that started banking trojan with worming capabilities for infecting more devices on compromised networks via network share exploits and highly aggressive brute-force attacks against Active Directory admin accounts.
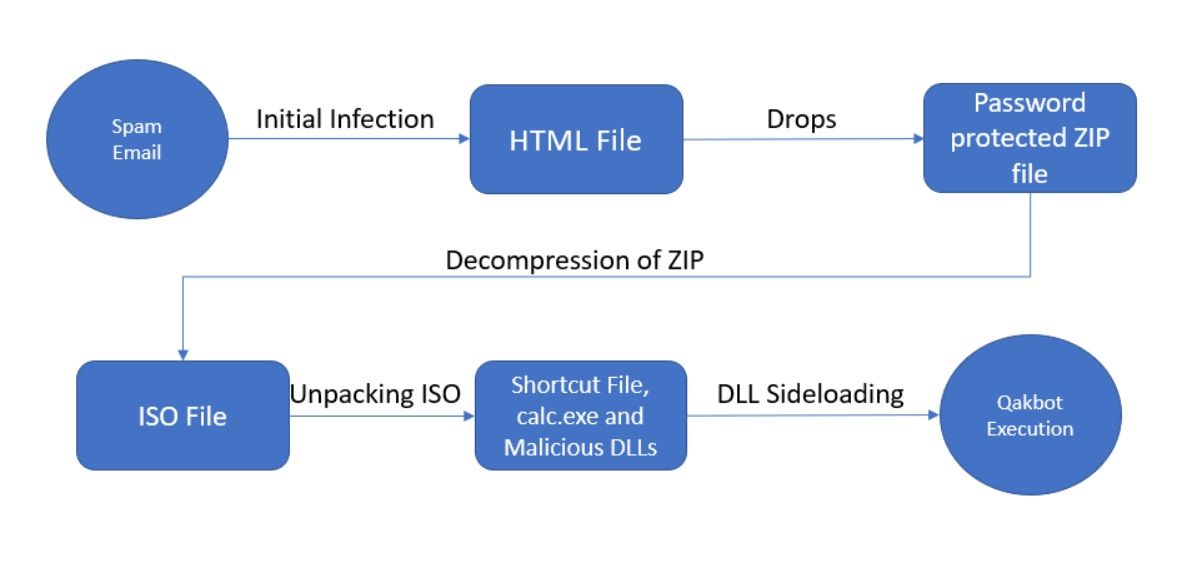
The attackers use hijacked email thread messages with HTML file attachments that have base64 encoded images and a password-protected ZIP file. After opening the HTML file, it will automatically drop the password-protected zip file in the Downloads location.
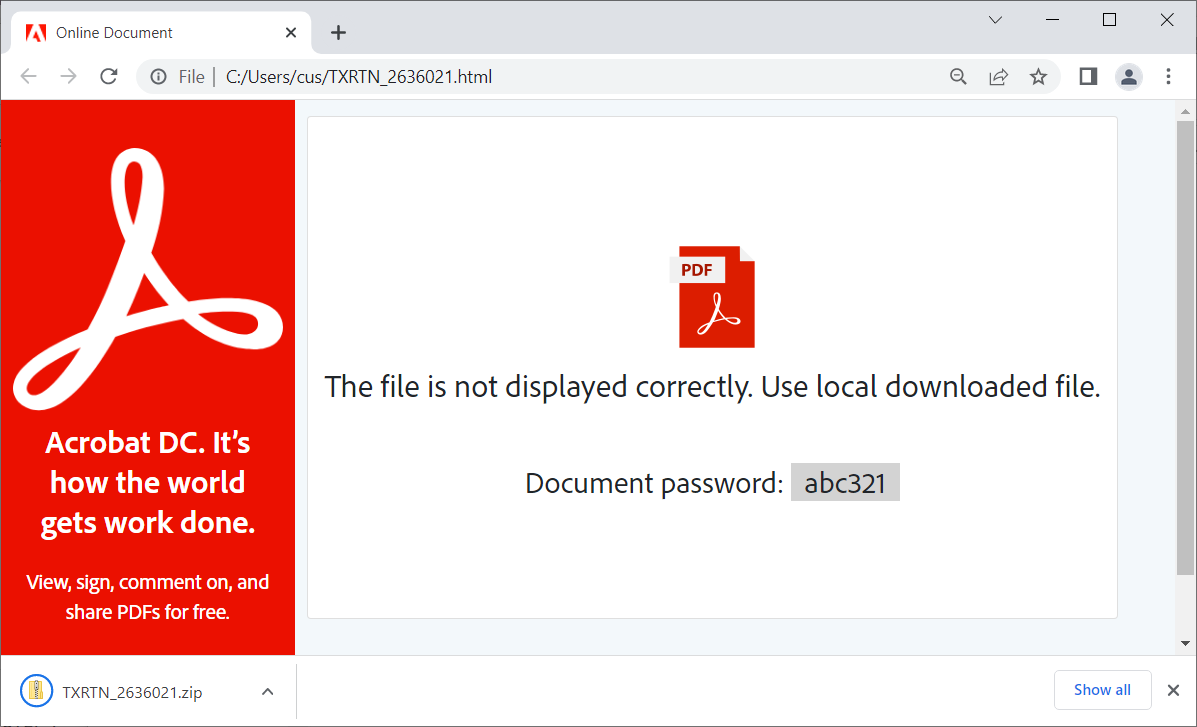
Upon opening the zip file using the password, it extracts another file from the folder containing an ISO image file named “Report Jul 14 47787.iso”. The ISO file contains four different files:
- a .lnk file
- a legitimate calc .exe
- WindowsCodecs.dll
- 7533.dll.
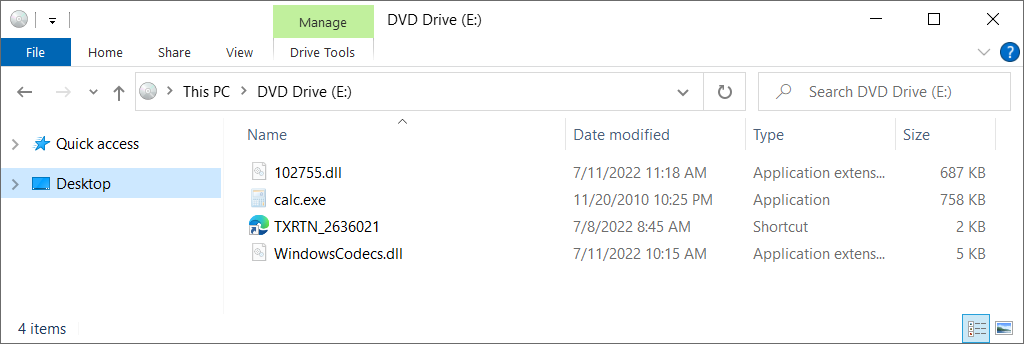
The.LNK file, which is disguised to appear like a PDF containing crucial information or a file that opens in Microsoft Edge, is the only thing that appears when the user mounts the ISO file. However, the shortcut's destination is the Windows Calculator app.
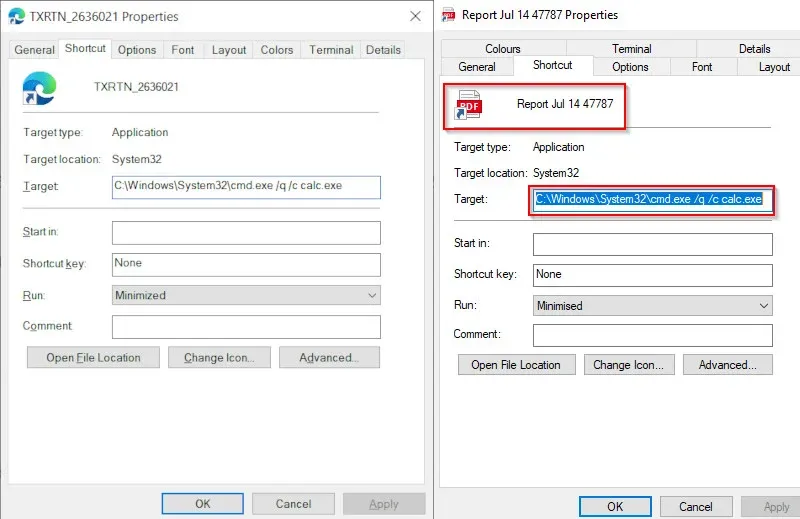
Analysts found that TAs exploit the DLL sideloading approach to run malicious code through legitimate apps. In this method, TAs combine trustworthy programs with malicious.dll files in a single directory. A genuine file loaded by the application during execution has the same name as the malicious.dll file. Using this approach, the attacker runs the malicious.dll file.
In this instance, the malicious file WindowsCodecs.dll poses as a support file for the application calc.exe. When calc.exe is run, WindowsCodec.dll is also loaded, and then regsvr32.exe is used to run the final Qakbot payload. The final payload carries out all harmful operations by injecting its malicious code into explorer.exe.
Indicator Of Compromise (IOCs)
SHA-256
- cb83a65a625a69bbae22d7dd87686dc2be8bd8a1f8bb40e318e20bc2a6c32a8e
- 9887e7a708b4fc3a91114f78ebfd8dcc2d5149fd9c3657872056ca3e5087626d
- 8760c4b4cc8fdcd144651d5ba02195d238950d3b70abd7d7e1e2d42b6bda9751
- c992296a35528b12b39052e8dedc74d42c6d96e5e63c0ac0ad9a5545ce4e8d7e
- f161a836afdfcf9341cae1cc806404ff178b061266e71e587117b987ed36029d
- bee0dc3779577ea5c89893a80135376260ca5cef46a81519c46fdf850035b709
- 37b033b692d48cb81b6e52c3967cac2a5f60c233228fe8d900545276c5d0fd5c
- 98d69b12a7881bf935236facc22eab1411f92cd7cb6e7355c0831a70889b32c9
- 5b67702e6589f0e6765f7b0c240756386a1af9979ac3f15596fb2eebb06aa6a6
- fcf8a2c87fea4a97540f011bfc671ed074b84dc517588669b20b226f71e2b115
- 5777a25b5b01abcefbf1e02e631591d6f3f92d80115189eff360d0874e9bb6a9
- 87b2ded9fc94d4a4c9daec054cafb0ff3cd731b076ac552c71995f66392b715e
- bd9d8a7d55c1cf8d2eb1e9f4a72f79fe72139a3ebd7052b1a1182114e32effd8
- f88a8ddb6f5b0e4f9988b1673a4fd3ee2b75563d512f8faf2322e69e5d705c84
- 6c726c70e616838a7d869ab25d587a1d71843eda3f4d7fdfca30a6cc933b1610
- ffe987476e77de540b6ca1ce8ebe715cd6bd20a96efa8299c7d108be8ab56eaa
- 2bf08deca09bd82e9f33cab888b1802ab2acbad79cbf84413ee7864bbe2849ae
- 880e1cd2c68fb420643c5e14e78a48183b146cef4eecb1f4876f9993df2ac634
- 914ffbfd472d1155e50400724fb120bb65b8af5def64ee86212c16034721ad5d
- 973fd3c6ac4221d7c6586973c5a4414465c7a9f61044713aa7c22e81bb20ceec
- 77eac682c90c329bb1ddfe288912a2031cebd64fdb0f3a4715b2e750eb622df9
- 22ba81244e68afbe85f54cec0ade1834b8a4d6c2146dbffa61226c05e54f584e
- aad0537d91ef02de4daa80d105bd457645e932fa96b35ca6f89e17e5f79773fb
- e73eec83f2675d3ba971f0c7bbd79843543cfa99cd7e06a23a0a78c984d91379
- e55d81b2b5151e2064db37f2acd23bfe301b4e9da4f6714deacba923c5bc57ab
- 003ed7945a0247b703eb5e4866233ab9f747c5995e18b1cd8fd6e31b0a7c6111
- c13320b6e8b708c54089664e6ddb5bd0f019591027e2dd871d551a0e8f7bcdda
- 6a2e228c5e79aa66e3585993560886213c6bb58ec864b2d41ada8353eadbedc1



