New variant of IcedID malware
According to Proofpoint, Researchers discovered a low-volume operation spreading IcedID versions that don't contain the typical online banking fraud capabilities and instead concentrate on infecting infected devices with more malware.
New variant
When the malware loader originally surfaced, it was immediately transmitted through countless customized phishing emails with invoice themes. These communications employed malicious HTA files that, in turn, ran PowerShell commands to fetch IcedID from a remote resource via Microsoft OneNote attachments (.one). The victim also receives a PDF that is a fake at the same moment.
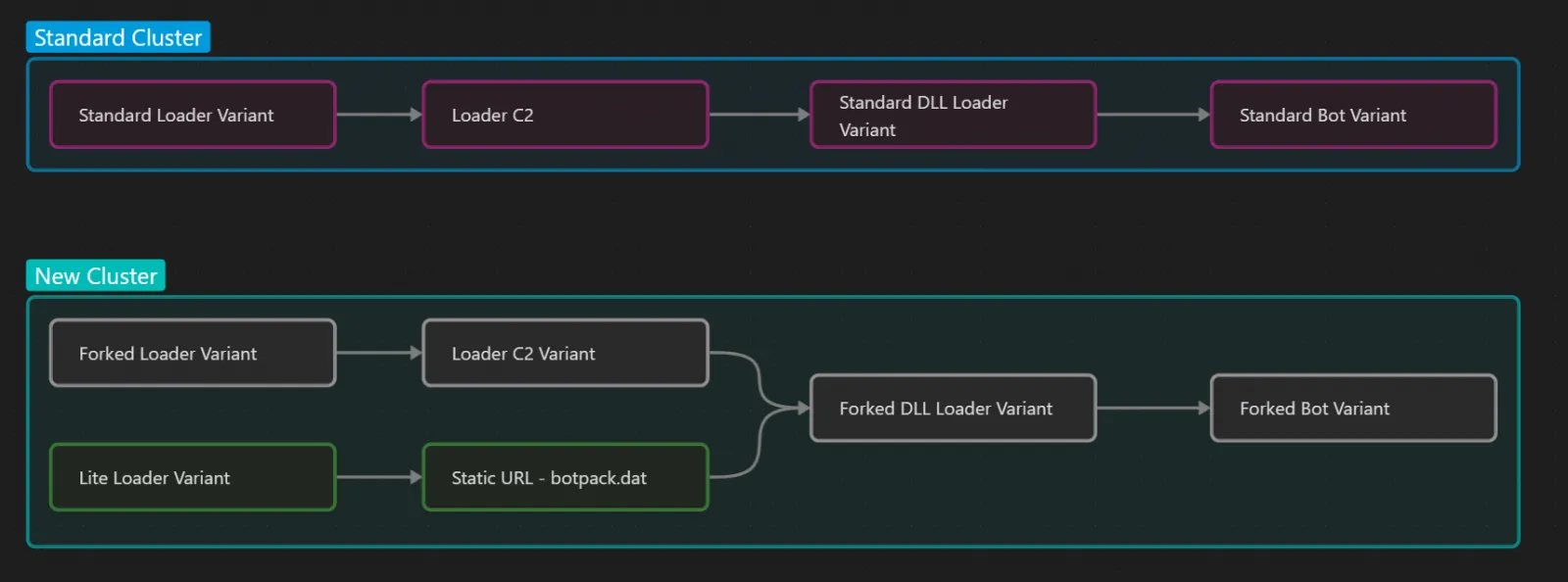
The "Forked" IcedID loader performs a similar function to the "Regular" one, delivering the C2 the necessary host information before fetching the IcedID bot. Nevertheless, "Forked" has a payload that is "Normal" due to the use of a new file type (COM Server) and the insertion of domain and string-decryption code.
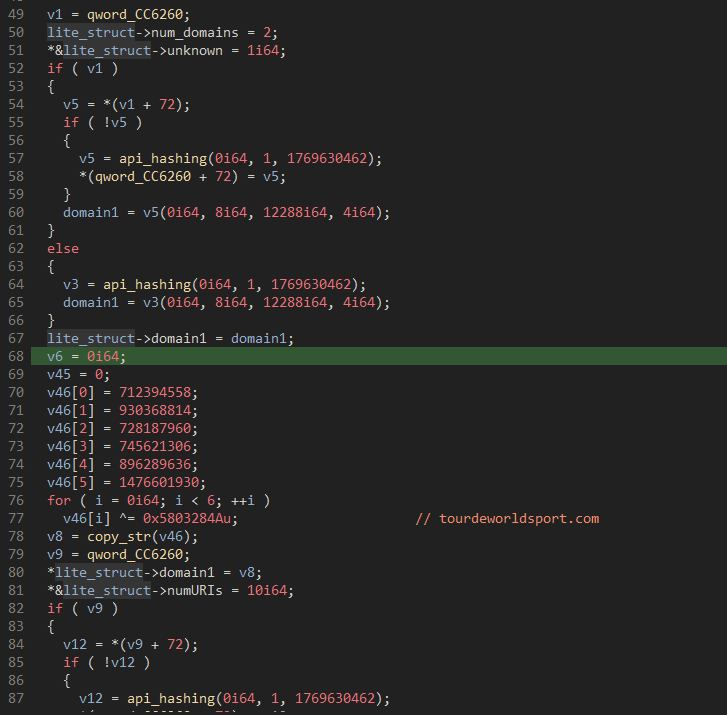
The "Light" loader variation, on the other hand, is 20KB lighter and does not leak host information to the C2. Given that it was deployed alongside Emotet, which had already profiled the compromised system, this change makes sense. The emergence of new variants of IcedID, which indicate a shift towards specializing the bot to payload delivery, is concerning because threat actors typically use IcedID for initial access.
Indicators of Compromise
File Hashes (SHA256)
- 74b6f79cbbd934feb5b3aedb20c7b627375f6264e7a6ac0fec4f577deee180aa
- 866d1026d90fa0a28c8a17278660476a9c78f4567894adfa86f59a734c07696a
- 753937151d98a59821e897916e893f5ab3612388a8fdc76f86b493b004e0fd43
- 9aa827a7db442498a10bbba907c1ce79b9579b85914368d4facf1d7adb52330d
- b8c3b7519abeb80d0746fbde5a9cf0d53f1bb8896807ccccbf8d66e683b63216
- fd77f3d120cdda8531722d2df8874cb17c7c1fecb7bf7478f9b947b1768c73d8
- 6d1c7e322097b33ffaf3dff98ffc5058d90b5c5f7016f481ae384b0eb93c7001
- 60fd7ccfa78c074c0f70a72202cff67b4000013f3f433b4e273ed3c7864eeb8d
- 0cc54d6cbc23dadf68d9d1354881e46346ec6aab29b1de2474e034ead8230ee5
- 68645c3da7534c5596abd0cdf93f30af3f5bf7c96c086b018fe8f8d6ffb31315
- 9959cac38d12b50044f081d16343ba887b419d256c8bb85b43d185350e84b32b
- 4cc1683bc29947d7aa160d0c43100e5a3ad405a8727980d1be34e8f1ee833efe
- a2158fb6574d9d8f473eee19b6cba91f2d5c0fc5289e9245bb4d290380e22226
- 35ef1bb985e0164d698f2c66706141a8f6c87d57f02ece42a50bc4ea1e2cd8d1
- 866011c18e7db2ad7203600a59f050654787aef69741b718a8f6d938260245b5
- 1cada6c3166a8db10461cc53ac55985d646422a4c69665c2b6952719b4fc4a7f
- c139cc51b09e6a0c0415b665c3cec704299cca185f5f7c9e239bdf82e3911245
- 614d5b61e6ab5a7eaca271bee897127f4d01b593be36c15eead7afd8b47db177
- 05d7d343a5ed256ef1217c92b75f444bc6fb3a0cabbcf000dd8e9211c0bc4a28
- 89199d2930d772ea214eb58cd88c9615a1d504c127cd49ef0903e83362c4dcfa
Domains & Ip Address
- aproillionsgif[.]com
- utorsabegot[.]com
- ituitem[.]net
- ariopolanetyoa[.]com
- 13[.]107[.]4[.]50



