Microsoft warns of stealthy outlook vulnerability exploitation
Microsoft has released security updates to address CVE-2023-23397 as part of patch Tuesday. Guidance has been shared to customers discover indicators of compromise associated with a recently patched Outlook vulnerability.
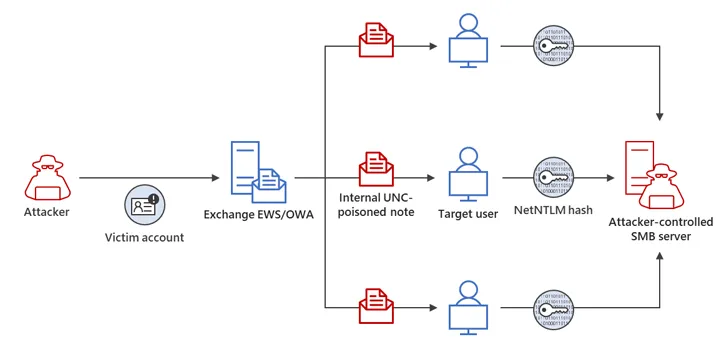
Analyst observed that the External attackers could send specially crafted emails that will cause a connection from the victim to an untrusted location of attackers' control. This will leak the Net-NTLMv2 hash of the victim to the untrusted network which an attacker can then relay to another service and authenticate as the victim.
The compromised email account was then used to extend the adversary's access within the compromised environment by sending additional malicious messages to target other members of the same organization. While leveraging NTLMv2 hashes to gain unauthorized access to resources.
SMBClient event logging, Process Creation events, and other available network telemetry should be reviewed to identify potential exploitation via CVE-2023-23397. Any authentications using NTLMv2 originating from unknown or untrusted IP addresses should be further examined.
If a threat actor attempts to access email for a compromised user, SoapActions including “ResolveNames”,”GetDelegate”,”GetFolder”,”FindFolder”,”FindItem”, and “GetItem” may be observed for the combination of the authenticated user and IP address. The following Kusto Query Language (KQL) query can assist with parsing and summarizing EWS logging for the purposes, if the relevant logs have been ingested into Azure Data Explorer.
The vulnerability CVE-2023-23397 was resolved by Microsoft as part of its Patch Tuesday updates for March 2023, but not before Russia-based threat actors weaponized the flaw in attacks targeting government, transportation, energy, and military sectors in Europe.
Indicators of Compromise
Ip Address
- 101[.]255[.]119[.]42
- 213[.]32[.]252[.]221
- 113[.]160[.]234[.]229



