A WiFi protocol weakness enables attackers to manipulate network traffic.
Researchers in the field of cybersecurity have identified a critical security hole in the IEEE 802.11 WiFi protocol standard that enables attackers to mislead access points into exposing network packets in plaintext.
The source and destination MAC addresses, as well as control and management data, are all contained in WiFi frames, which are data containers made up of a header, data payload, and trailer.
All frames intended for a client station (receiving device) are queued when it goes into sleep mode because it sends a frame to the access point with a header that includes the power-saving flag.
A hacker might impersonate a network device's MAC address and transmit power-saving frames to access points, making them start queuing up frames for the intended target. To obtain the frame stack, the attacker then sends a wake-up frame.
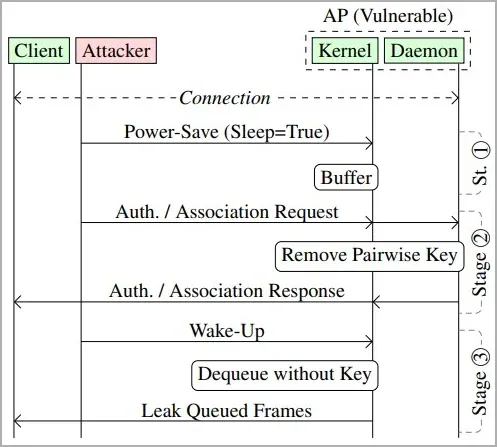
Typically, the WiFi network's group-addressed encryption key or a pairwise encryption key, which is specific to each device and is used to encrypt frames sent between two devices, are used to encrypt the transmitted frames.
By providing authentication and association frames to the access point, the attacker can, however, force it to transmit the frames in plaintext or encrypt them using a key provided by the attacker, changing the security context of the frames.
The researchers issue a warning that malicious material, such JavaScript, could be injected into TCP packets using these methods. The researchers warn that an adversary could use their own server that is connected to the Internet to inject data into this TCP connection by injecting off-path TCP packets with a spoofed sender IP address.
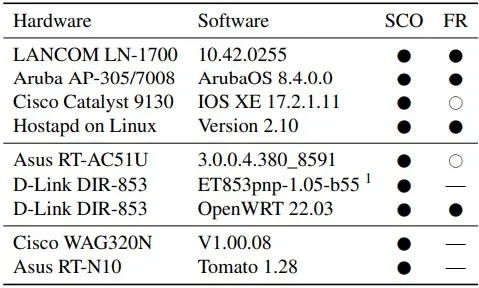
This might be used, for example, to deliver malicious JavaScript code to the victim over plaintext HTTP connections in order to take advantage of browser flaws in the client. Due to the fact that the majority of web traffic is TLS encrypted, this technique may also be used to snoop on traffic, but the impact would be minimal.



